kubernetes-training
Certificates
- Server cert: configured on the server
- Client cert: configured by client
- Root cert: configured by CA server
[!Note] Private key have
keyin them
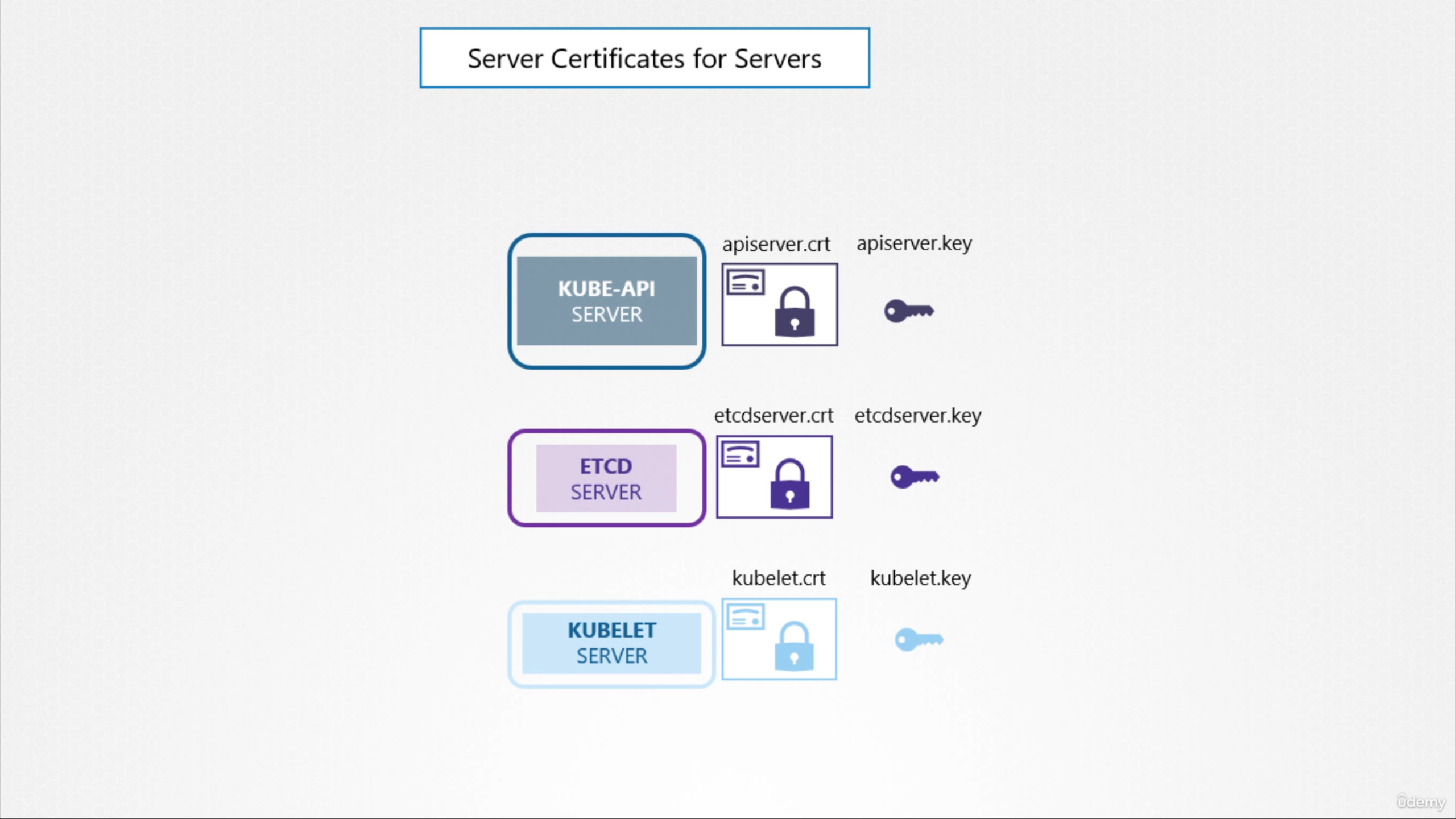
Server Certificate
- Kube-api server: crt and key, exposes https api service
- ETCD server: crt and key
- Kubelet server: on worker node, exposes an https api that the kube-api server talks to
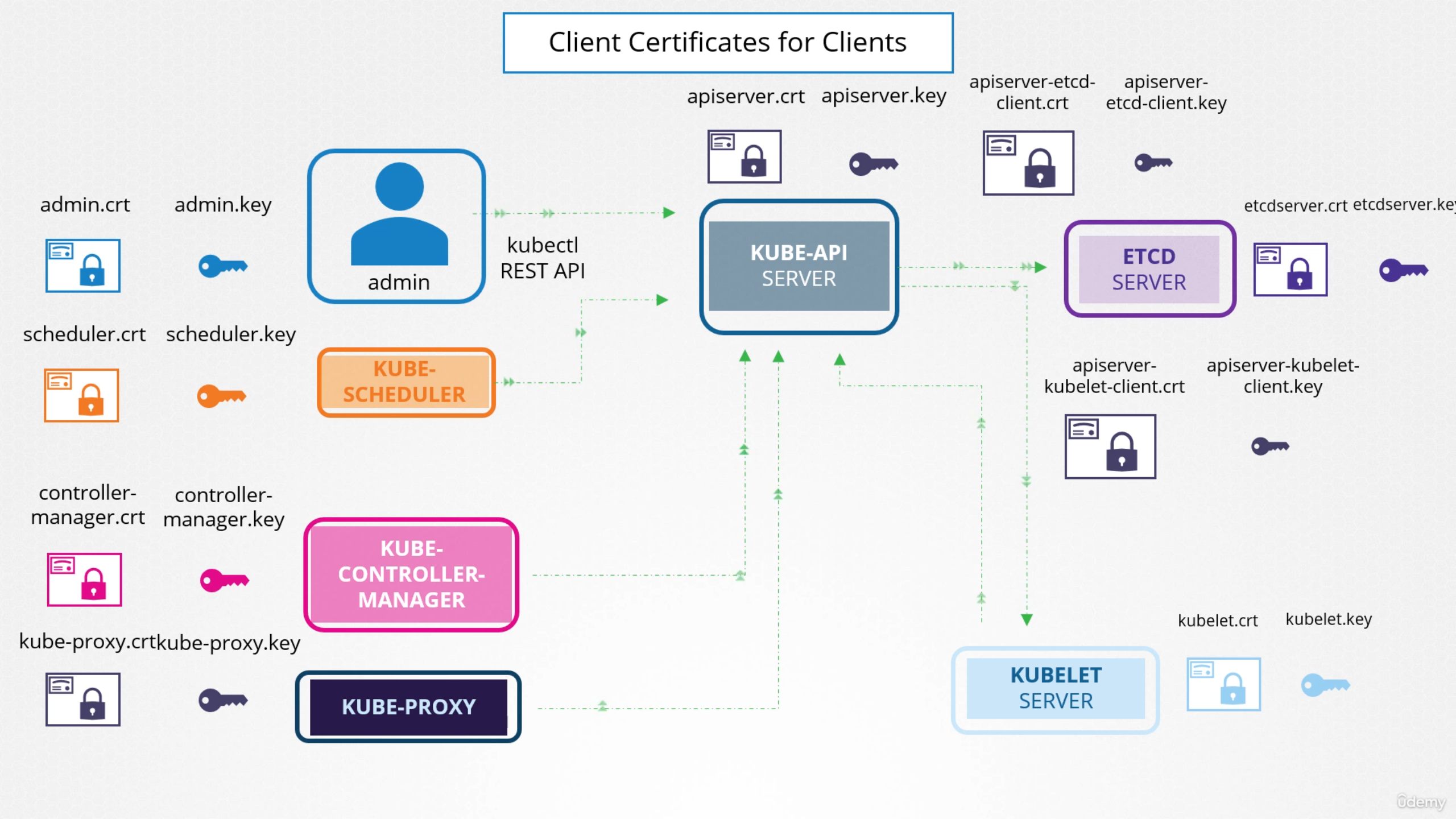
Client Certificate
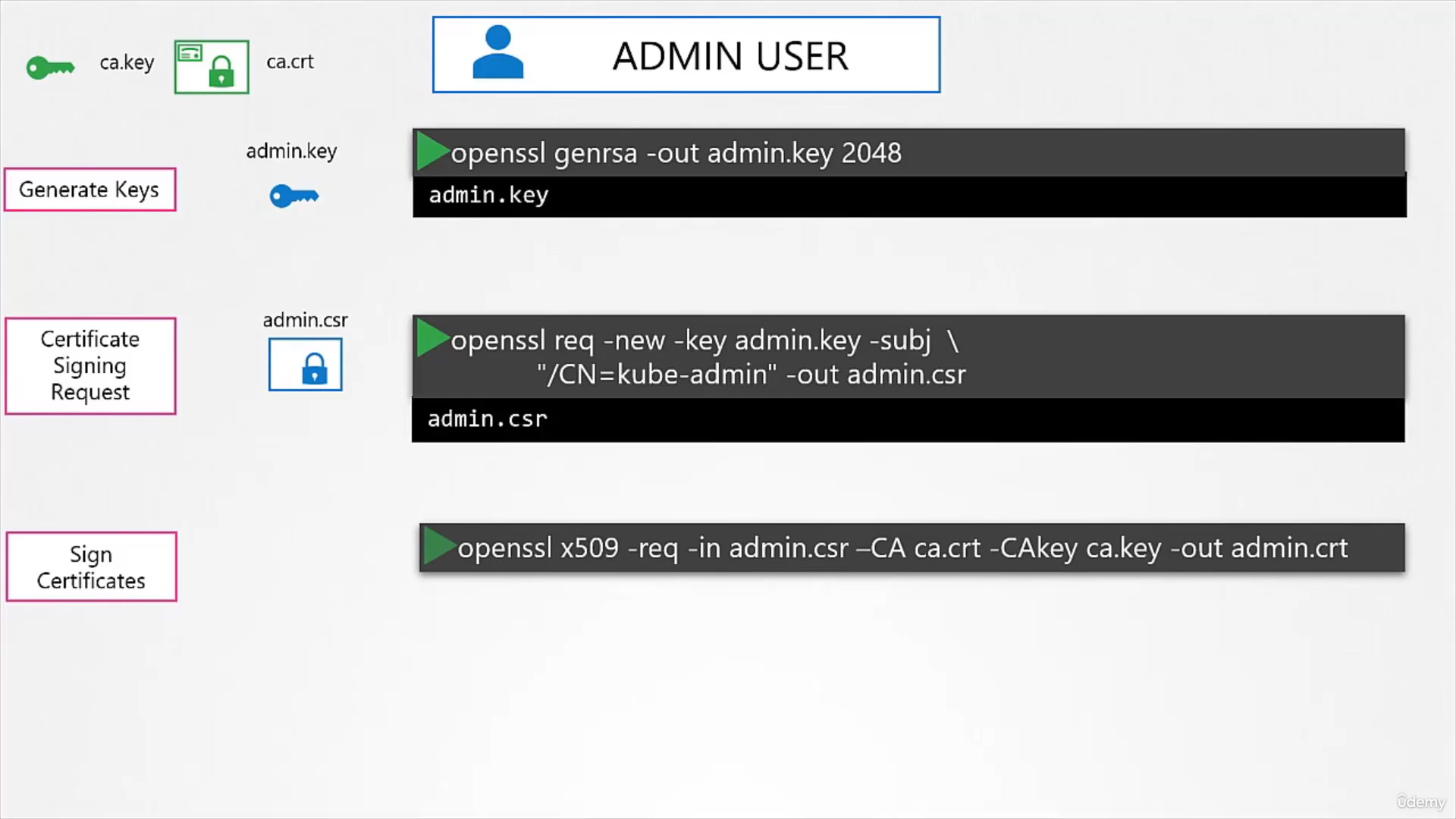
- Admin: needs crt and key pair to authenticate to the kube-api server
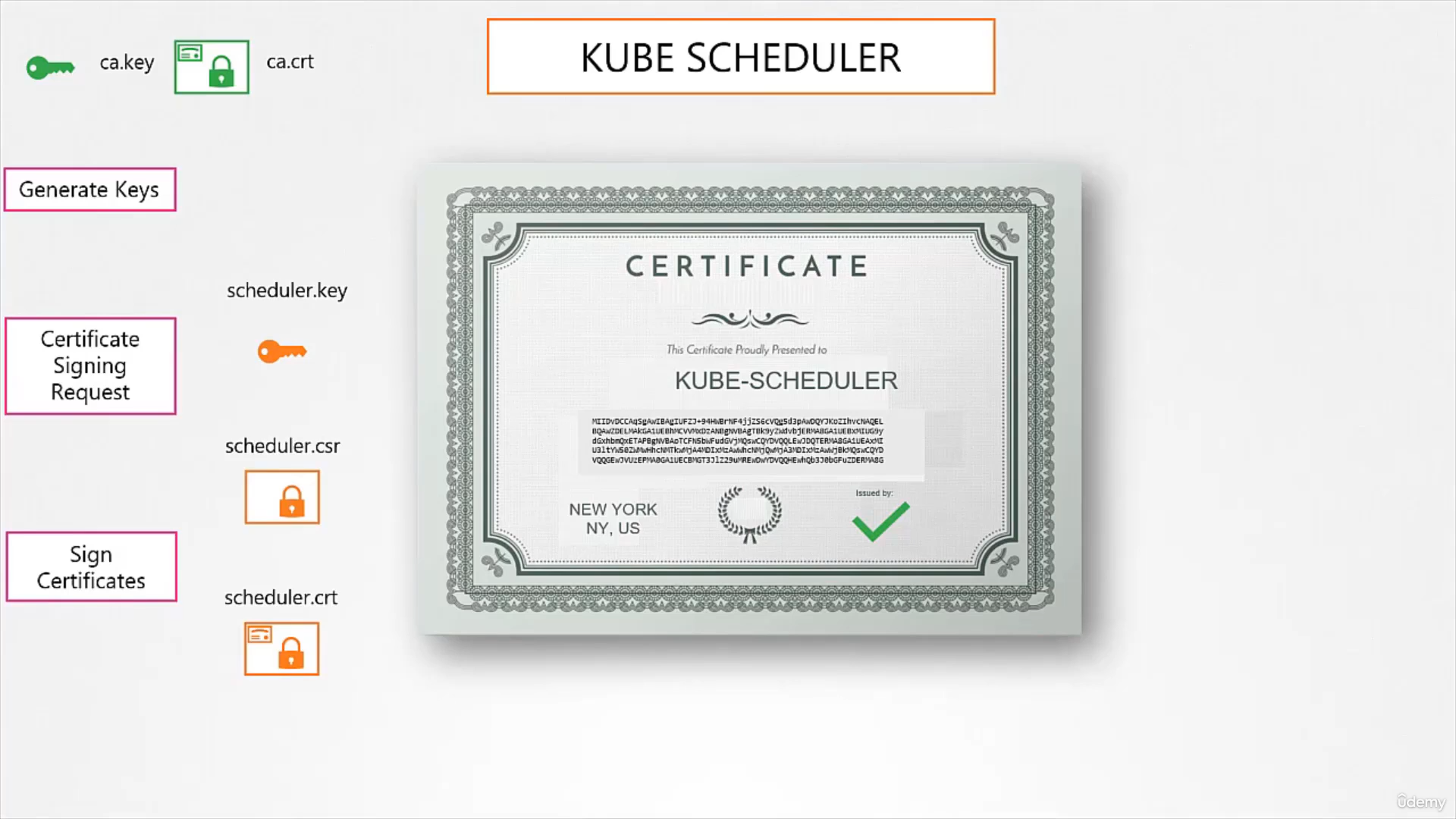
- Kube-Scheduler: is client to kube-api server. It talks to kube-api server to look for pods that need scheduling .
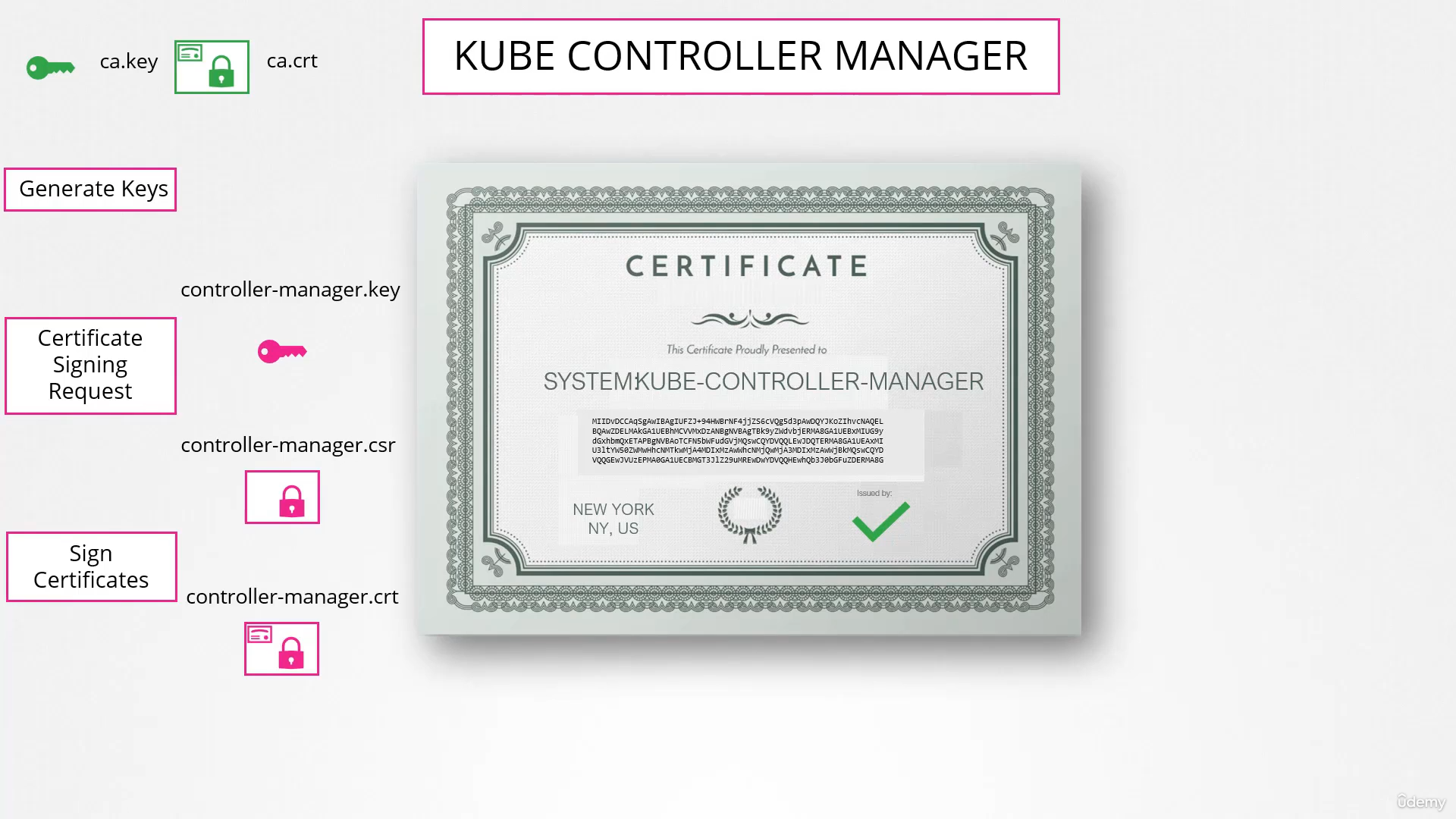
- Kube-Controller-Manager: is also a client to kube-api server
- Kube-proxy: also a client to kube-api server
- Kube-api-server: is the only client to the ETCD server
- Kube-api-server: also talk to kubelet on each individual node. That’s how it monitors the worker’s node.
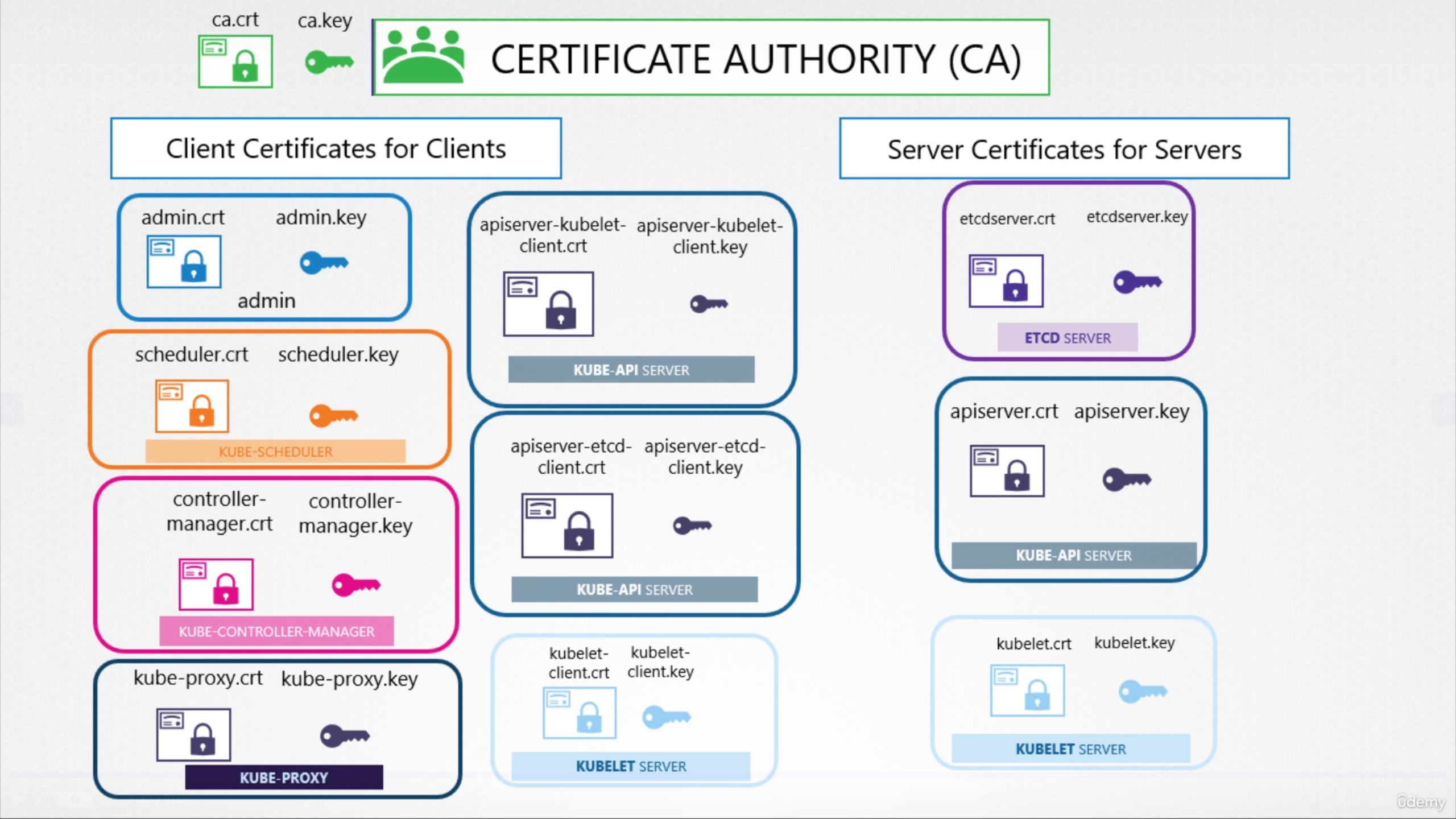
CA
- You’re required to have at least one CA for your cluster
- There could be one CA for ETCD, one for the rest of the cluster
Certificate Creation
Certificate Authority (CA)
- Generate keys
openssl genrsa -out ca.key 2048 --> this will give ca.key - Certificate Signing Request: all signing details w/o signatures
openssl req -new -key ca.key -subj "CN=KUBERNETES-CA" -out ca.csr - Sign certificates
openssl x509 -req -in ca.csr -signkey ca.key -out ca.crt
Client Certificate
Same procedure, the only difference is when doing Sign Certificates, you specify CA cert and CA key
Kube Scheduler
Kube-Controller-Manager
Kube-proxy: similar to controller mnger and admin
[!Note] For client to be able to be verified using certificates, all components of the cluster needs a copy of the public cert of the CA
Kubelet (being client talking to kubeapi-server)
- Same with system’s component: name starts with
system:node Server Certificate
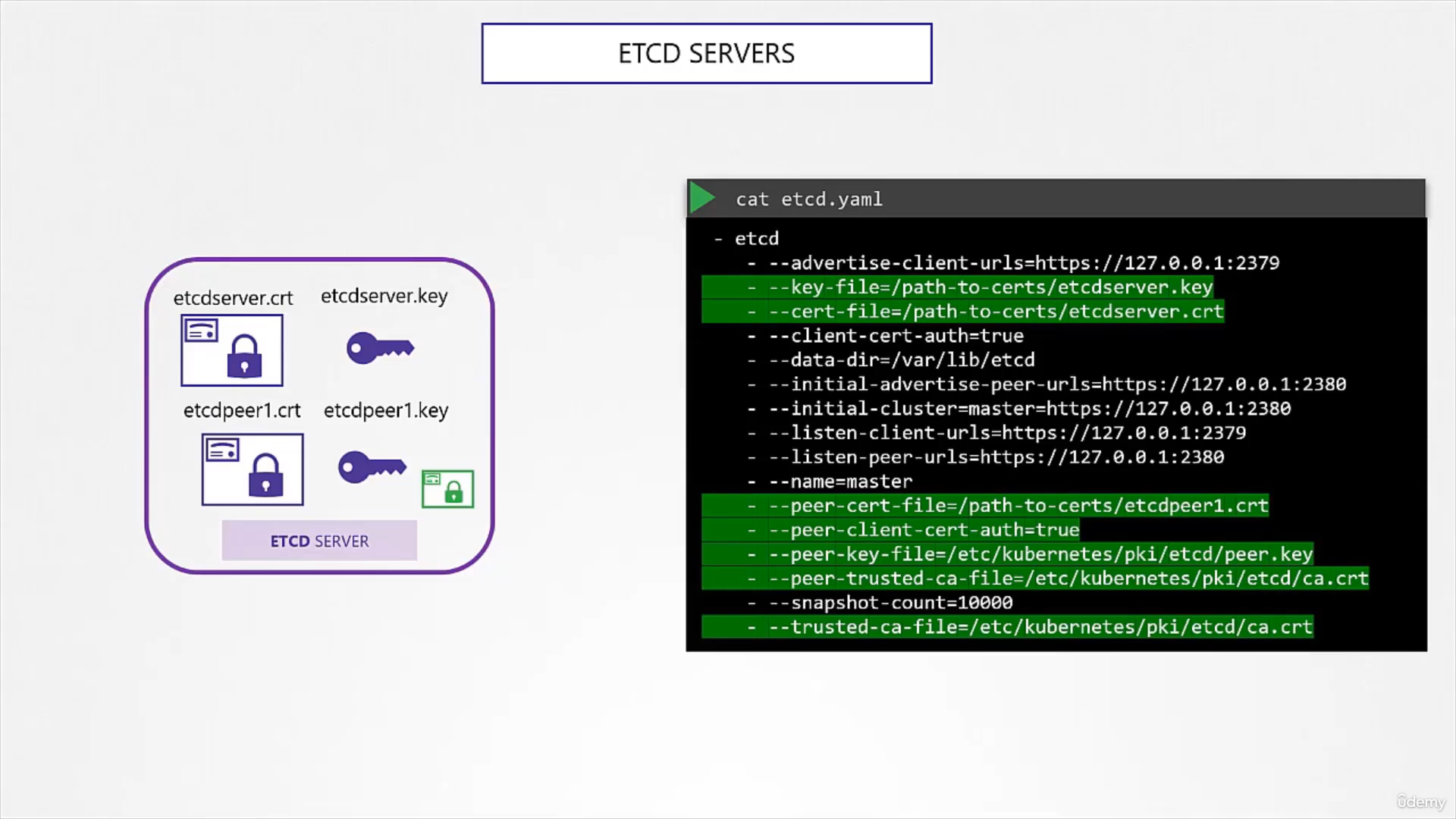
ETCD server
- Besides being a server, they also need peer server for HA
- Key, Crt, and trusted-ca-file (public root cert.) must be specified
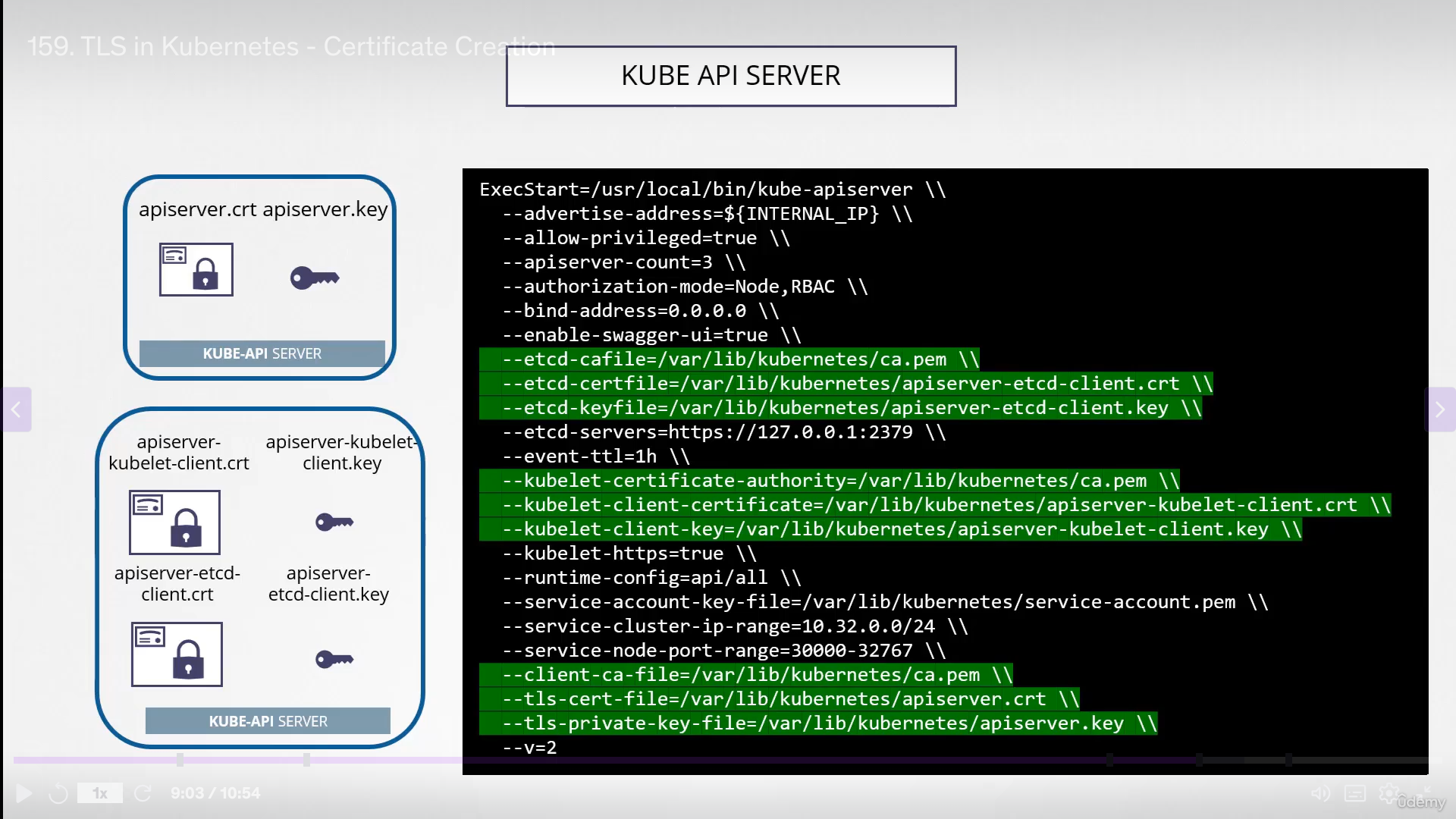
kube api server
- All the aliases must be configured in the cert by passing in
-config openssl.confin generating certificate signing requestopenssl req -new -key apiserver.key -subj "CN=kube-apiserver" -out apiserver.csr\ -config openssl.cnf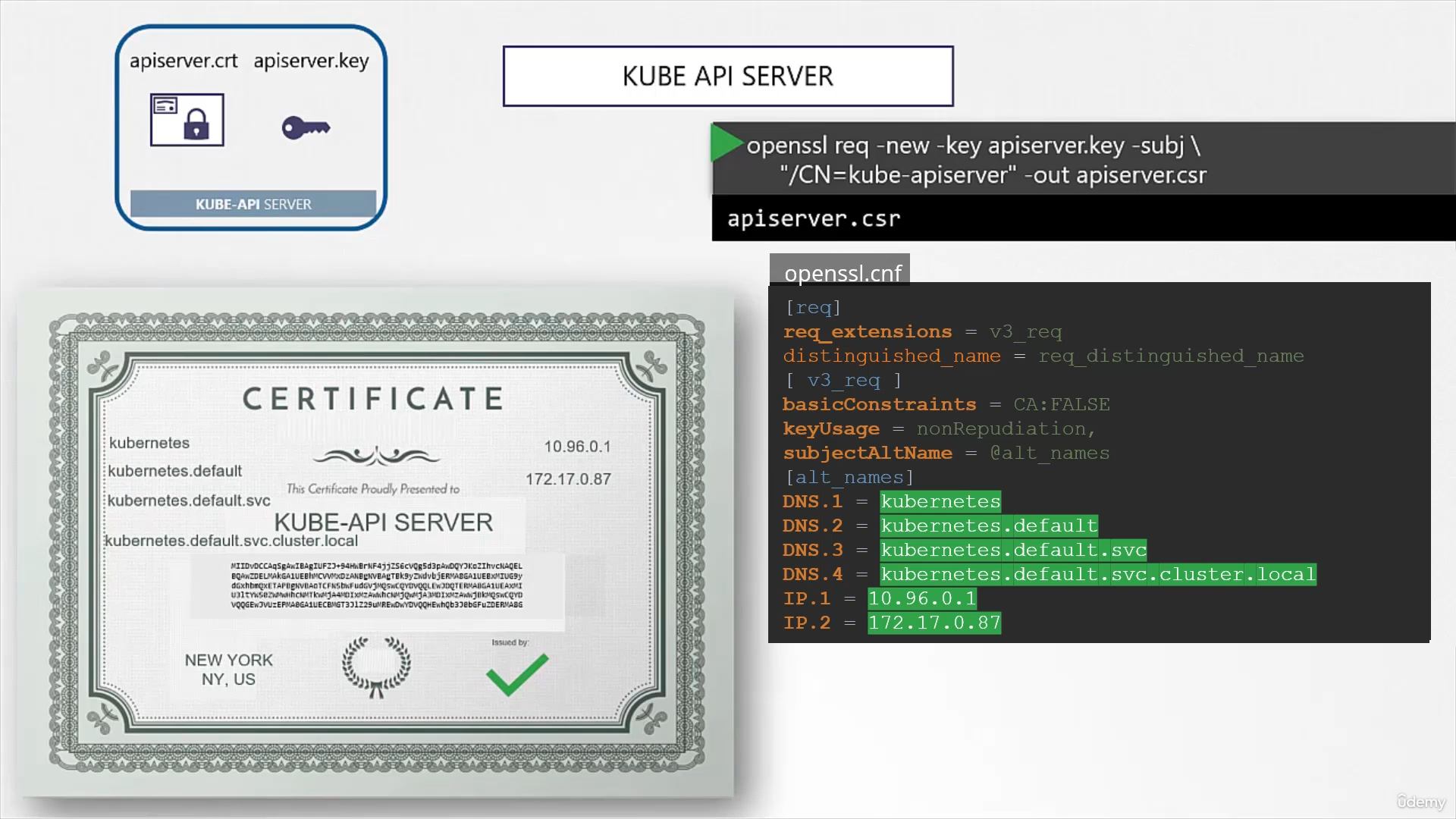
- Finally, sign the cert:
openssl x509 -req -in apiserver.csr \ -CA ca.crt -CAkey ca.key -out apisever.crt - In the executable used to configure kube-apiserver service configuration file :
- acting as client to communicate with kubelet and etcd: ca file, crt, key
- as server: ca file, cert and key
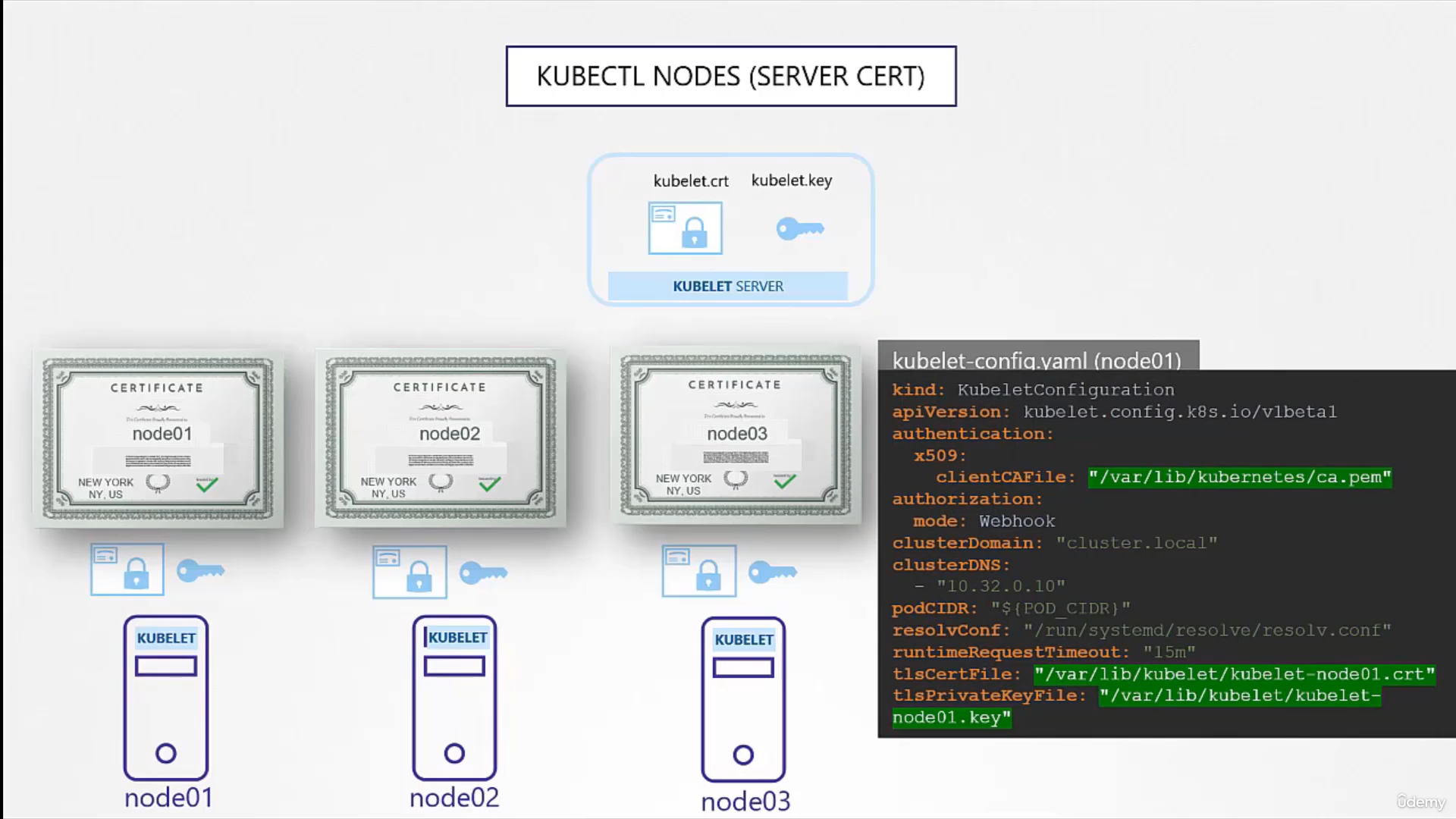
kubelet server
- https server that runs on each node, responsible for managing the node
- Each node should have its own kube-let.config with the ca file, the certificate, and the key
How to use cert?
- To authenticate with kube-api server
curl https://kube-apiserver:6443/api/v1/pods \
--key admin.key --cert admin.crt --cacert ca.crt
- Use them in
kube-config.yaml
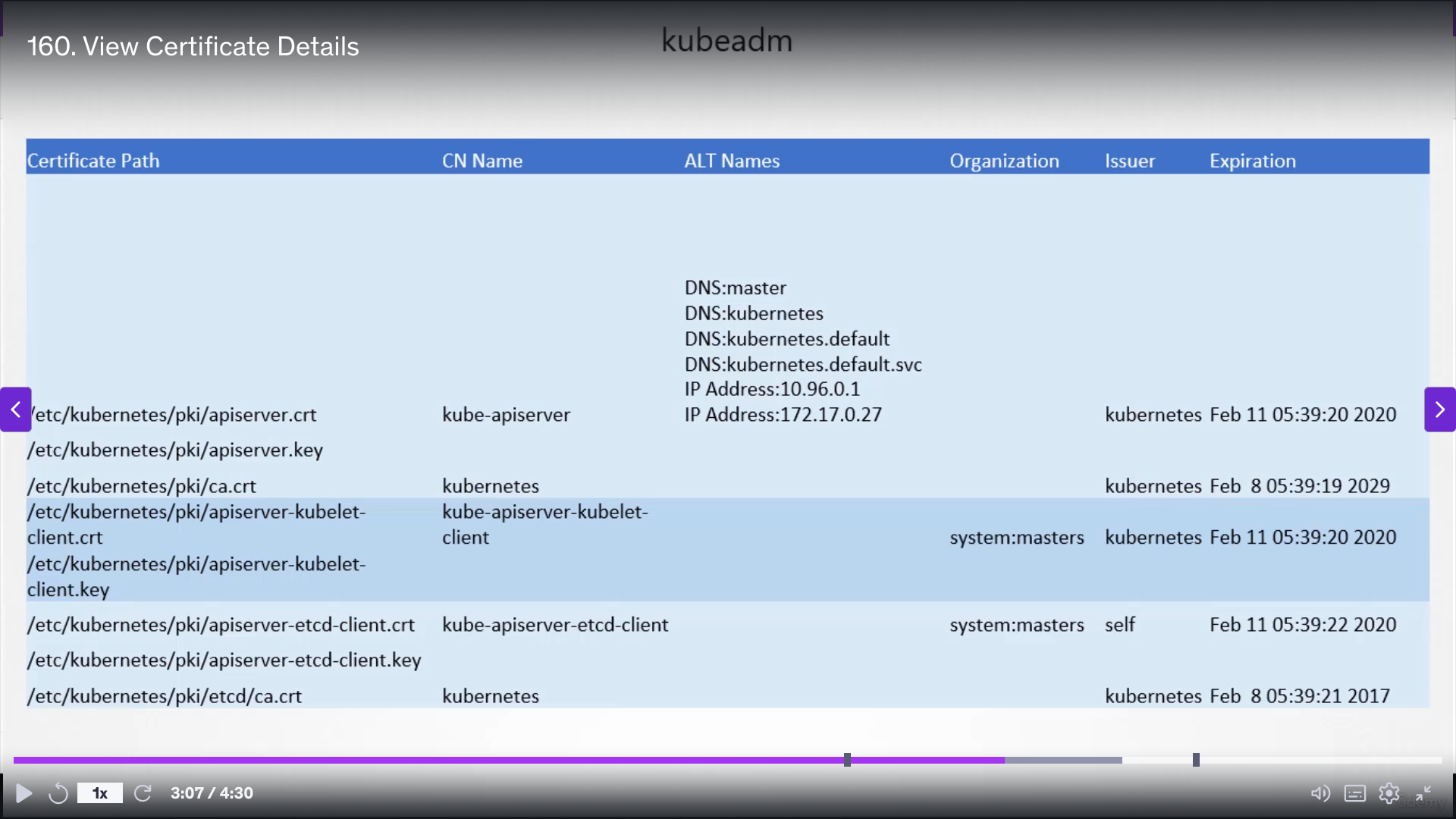
View Cert
openssl x509 in /etc/kubernetes/pki/apiserver.crt -text -noout
Healthcheck
- Using journalctl :
journalctl -u etcd.service -l kubectl log etcd-master- When kube-api-server and kubelet is down, follow procedure to check docker container